Oct
25
TTT Part 23 of n – Networking Intro
Filed Under Computers & Tech, System Administration on October 25, 2014 | 11 Comments
This instalment is the first in what will probably be quite a long mini-series on computer networking. Before we can look at the terminal commands that allow us to interact with the network, we need to gain an understanding of how computer networking works. This is a complex topic, ad there’s a lot to take in. The individual pieces don’t make sense without keeping the big-picture in mind, and yet the big picture doesn’t gel together until you start to understand the detail. Bearing that in mind, this instalment starts the series with a big-picture overview. We’ll flesh this overview out over the instalments that follow, adding in the detail that will hopefully make the whole thing click for you. Ultimately, it’s actually a very elegant design, but that elegance may not be immediately obvious!
Oct
24
“Behind People’s Backs”
Filed Under Computers & Tech, Security on October 24, 2014 | 2 Comments
I’m fed up with people being dishonest about the new search feature in Yosemite. You can have reasonable discussions about the pros and cons of this feature, but for goodness sake enough with the fact-free hyperbole.
I’ve lost count of how many people insist Apple is sending this information back to Apple “behind people’s backs”. Sorry, but that is a fact-free assertion. The screenshot below shows the search feature in question:

Here it is again with the important aspects highlighted:
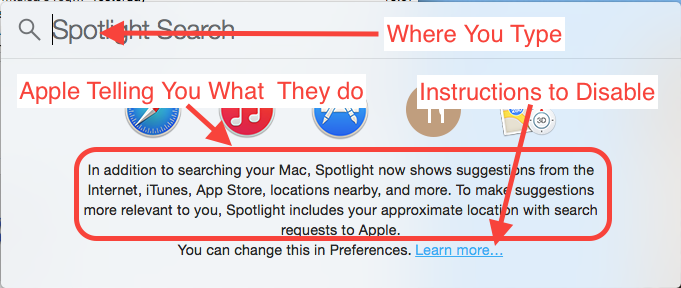
If that’s “behind people’s backs” then I’m the pope!
Something I will agree with critics on is that I think that link to instructions should be a button or checkbox to disable the feature. A link to instructions is nice, a button would be perfect!
This data is not being sent for no reason, it’s being sent to offer people a richer search experience, and Apple were actually playing catchup in this regard. Here’s what Microsoft say Windows 8.1 does:
By default, the Search charm searches the apps, files, and settings on your PC and OneDrive, plus the web.
The real question is whether or not Apple have thought about our privacy when implementing this feature, and whether or not they have designed the feature well. Here is what Apple say they do:
We are absolutely committed to protecting our users’ privacy and have built privacy right into our products. For Spotlight Suggestions we minimize the amount of information sent to Apple. Apple doesn’t retain IP addresses from users’ devices. Spotlight blurs the location on the device so it never sends an exact location to Apple. Spotlight doesn’t use a persistent identifier, so a user’s search history can’t be created by Apple or anyone else. Apple devices only use a temporary anonymous session ID for a 15-minute period before the ID is discarded.
We also worked closely with Microsoft to protect our users’ privacy. Apple forwards only commonly searched terms and only city-level location information to Bing. Microsoft does not store search queries or receive users’ IP addresses.
You can also easily opt out of Spotlight Suggestions, Bing or Location Services for Spotlight.
So, your searches are not tied to your Apple ID or any other persistent ID, instead, your device creates a new random identifier every 15 minutes, so your searches are anonymous, and most importantly, they can’t be profiled because the IDs are ephemeral. The fact that the device fuzzes the location before sending it on is also very good. The fact that IP details are not logged is also good. Finally, the fact that only a sub-set of the request is sent on to Bing is great.
I do not believe Apple would blatantly lie to users. For a start, as a publicly traded company that would almost certainly be criminal, but even leaving that aside, it would be spectacularly damaging for Apple to be caught lying about stuff like this.
Bottom line, Apple have been very open about this, Apple have implemented this feature with privacy in mind, and this feature is not unique to Apple OSes. Finally, if you want to opt-out, you can.
If this really is such a scandal, why is Windows 8.1 not coming under the same fire? *cough* link bait *cough*
Oct
10
TTT Part 22 of n – Tips & Tricks
Filed Under System Administration, Computers & Tech on October 10, 2014 | 2 Comments
This instalment is a little breather between the fairly heavy instalments on searching, and the upcoming set of instalments on networking. We’ll start with a look at some tips and tricks for getting the most out of BASH, and then transition to some tips and tricks for getting the most out of the OS X Terminal app.
Oct
1
WW1 – Antwerp in 1914
Filed Under History & Geography on October 1, 2014 | 2 Comments

“Zeppelin bombing Antwerpen” by Ad Meskens – Own work. Licensed under Public domain via Wikimedia Commons.
One hundred years ago today, the siege of Antwerp was underway. It started on the 29th of September 1914, and the city did not capitulate until the 10th of October. Rather than re-tell the story of the siege, which you can read in so many places, I thought I’d share a Google Earth map I’ve spent the last six weeks creating showing the core infrastructure of the Antwerp area as it was in 1914. When reading about large-scale historical events, I like to use Google Earth to follow along with what I’m reading and get a sense of the local geography. The thing is, if you do that with the siege of Antwerp you may find it confusing to follow along because there have been some very significant changes in and around the city in the last 100 years.
In this post I’m going to detail some of the very big changes, but really, for the best experience, you want to download the KMZ file and explore it at your leisure in Google Earth. I’ve also included a substantial area to the west of the city in the map, as far as Ghent in fact, because this is the route along which the Belgian army successfully withdrew from the city as the siege neared its end.
The KMZ File
The KMZ file is broken into two primary sub-folders, one for outlines, and one for labels. The reason for this is that having the labels displayed while zoomed out makes the map too cluttered to get a good overview, so you can check both on or off independently.
On the map, military fortifications that were active in 1914 are shown in red, military inundations in purple, and large recently decommissioned (in 1914) military fortifications are shows in orange. Navigable waterways, be they rivers, canalised rivers, canals, or maritime canals, are shown in blue. Docks which existed in 1914 are shown by blue overlays, and any docks not overlaid did not exist in 1914. Railway lines that were active in 1914 are shown in green, as are important railway stations. Large railway yards are shown as green overlays.
There are details available on all the shown items. For waterways and railways, click on the green or blue line to see the descriptions, for military fortifications, railway stations, locks, and docks, click on the icons.
For the best experience I recommend disabling all the standard layers except for Borders and Labels. The roads and photos in particularly are very distracting, so I definitely recommend turning those off.
Below are some links to various tellings of the story of the siege of Antwerp:
- The Wikipedia page describing the siege
- A short description of the siege on firstworldwar.com
- Arthur Conan Doyle’s description of the siege
- A description of the siege on metalfloss.com






