Dec
1
Yet Another QuickTime Zero-Day Vulnerability
Filed Under Computers & Tech, Security on December 1, 2007 at 8:36 pm
Apple’s security reputation takes another dent this week with yet another zero-day exploit in its QuickTime media player. There is now proof-of-concept code out there which uses this exploit to remotely compromise computers running both Windows and Mac OS X. The vulnerability exists in QuickTime’s handling of media streamed over the RTSP protocol. If you are a bad guy all you have to do to use this exploit to attack someone is to get them to open a specially crafted RTSP URL (a url starting with rtsp://). If the victim’s browser has JavaScript enabled you can make things even easier for yourself, you can get JavaScript to open the RTSP URL for you! What this all means is that you can now have your Mac compromised by simply visiting a web page. This is a lot worse than the Trojan that I discussed a few weeks ago where you had to actually download and install a program giving it admin access in the process in order to be compromised. I should mention that this exploit does NOT give the attacker admin access to your machine, it ‘just’ lets the attacker run any code they want as the user running QuickTime. This is not as bad as an exploit which would allow the attacker to execute any command as root/admin but it’s still very bad.
You can get more details from US-CERT. That page also gives you some guidance on protecting yourself. However, those instructions are very windows-centric.
[tags]Apple, QuickTime, Zero Day Exploit[/tags]
Personally, I have chosen to deal with this problem by removing the association between RTSP URLs and QuickTime. The simplest way I have found to do this on OS X is by installing the RCDefaultApp system preference pane. Once you’ve downloaded the disk image mount it and then double-click in the file RCDefaultApp.prefPane. You will be asked whether you want to install this preference pane for all users or just the current users. Personally, I always install things for all users but bear in mind that you will need to enter your administrator password to do that. Once you’ve done this you’ll find that a new icon has appeared in your System Preferences App under ‘Other’.
To remove the association between RTSP URLs and QuickTime you need to open this preference pane go to the URLs tab and select RTSP from the list on the left-hand side. Then you need to change the default application to <disable> using the drop-down list on the right-hand side of the window.
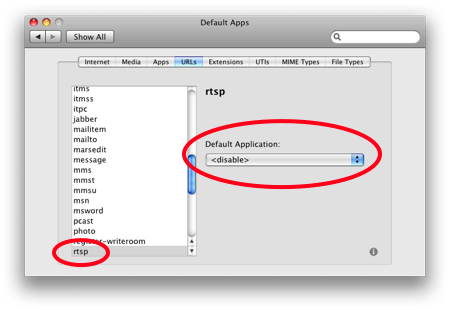
It is important to understand that removing the binding between RTSP URLs and QuickTime will only protect you from pages which would try to automatically open RTSP URLs. If you explicitly use QuickTime to view content over RTSP you are still vulnerable. Until Apple release a fix you need to be very wary of using QuickTime for playing streaming media.







[…] from Ron. Chit Chat Across the Pond with Bart Busschots covers a vulnerability in Quicktime, go to Bart’s Blog to download the preference pane to fix it. Turn off Auto Gain Control in Skype with the hack at […]
Hey Bart,
thanks for explaining how to prevent the automatic exploit of that thing. I had heard about the exploit itself before hearing it on allisons nosillacast, but i had no idea how to disable the automatic loading of rtsp. RCDefaultApp proves very useful in several ways. Thanks.
[…] problems caused by 7.4 in fancy stuff like Adobe After Effects. Reverse the instructions Bart gives here on his blog to let RTSP run […]